IoTVAS API: IoT/connected device discovery and vulnerability assessment API
You cannot control what you cannot see
- Proprietary protocols are often used for managing and monitoring IoT devices that are not known to the asset discovery solution.
- Agent based asset discovery is not possible because most of the IoT devices are resource constrained systems with proprietary operating systems that do not allow installation of discovery agent software on them.
- Device discovery is often limited to the devices with a history of known vulnerabilities.
- Fuzz testing method used by these solutions often time caused device operating system crash and reliability issues.
How does IoTVAS API discover devices and their risks?
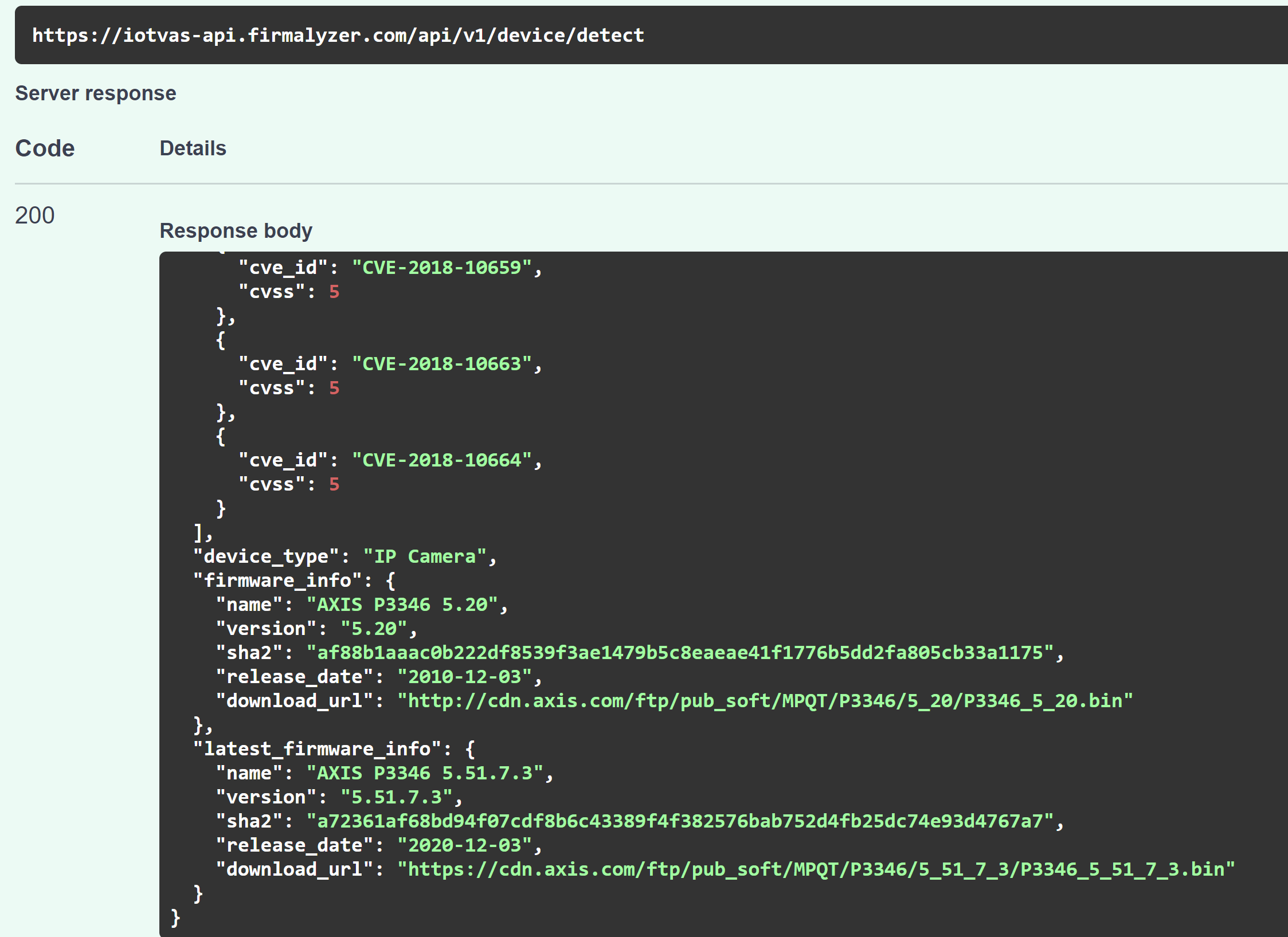
- Accurate identification of device manufacturer, model name, device type, device end of life status, firmware version and firmware release date
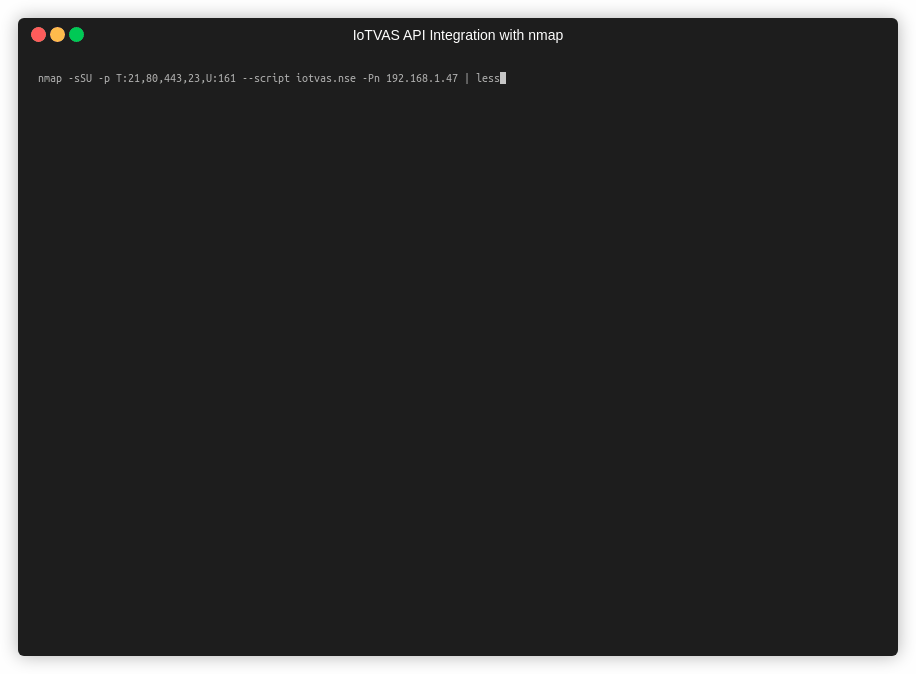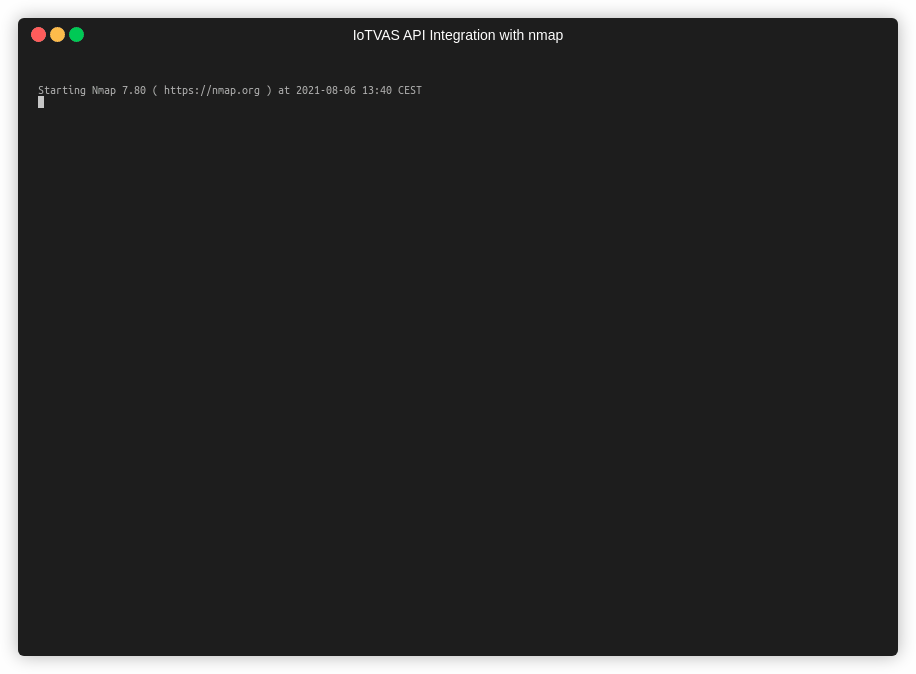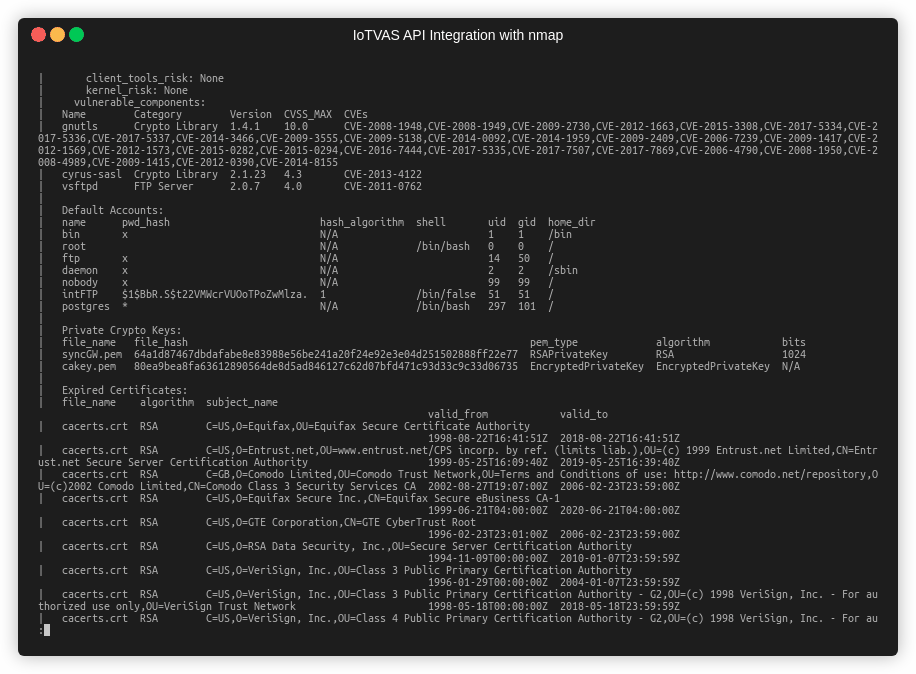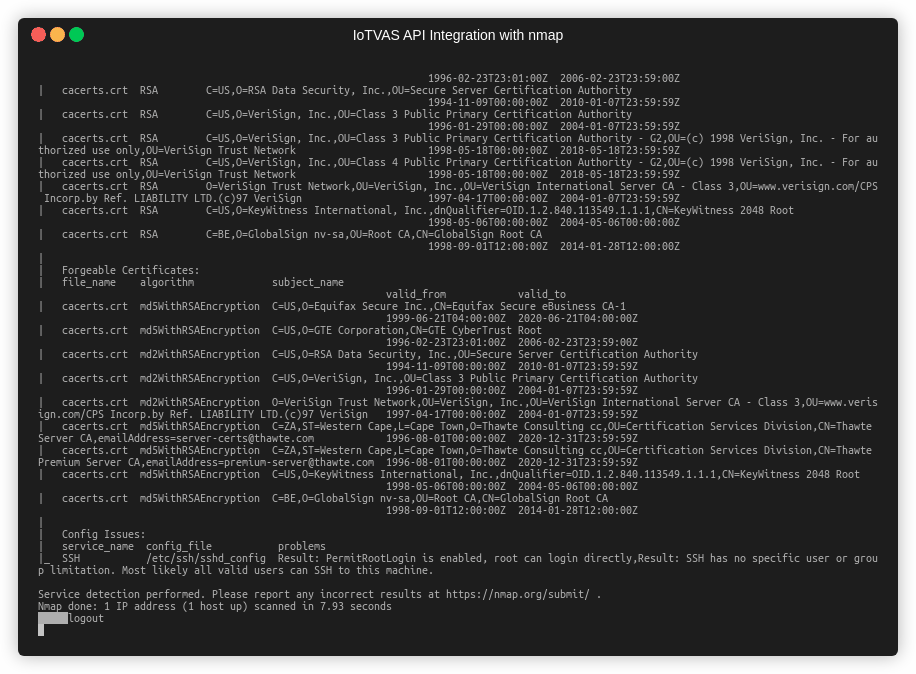
- Safe and in-depth vulnerability assessment of identified device including publicly known vulnerabilities (CVE) and unknown vulnerabilities in device firmware code including vulnerable 3rd party components, default credentials, crypto keys, certificates and default configuration issues
Key Advantages
Uses device fingerprints based on the network service banners of the device, hence there is no need for collection of the device network traffic
Identifies devices in the absence of their MAC addresses, hence it can detect remote devices in segmented networks and over the internet
Provides in-depth real-time device firmware risk analysis of the identified device without requiring the user to upload firmware file
Easy integration with industry standard security tools such as Nmap and OpenVAS