Discover IoT/connected devices, their CVEs and their firmware risks
IoTVAS extends the reach of your vulnerability management program to the IoT/connected devices. It can integrate with your existing IT asset management and vulnerability assessment solution, providing accurate device discovery and real-time vulnerability assessment at the firmware code level without requiring network traffic collection or installation of software agents on devices. This allows you to get the most of your existing security tools and proactively find high risk connected devices.

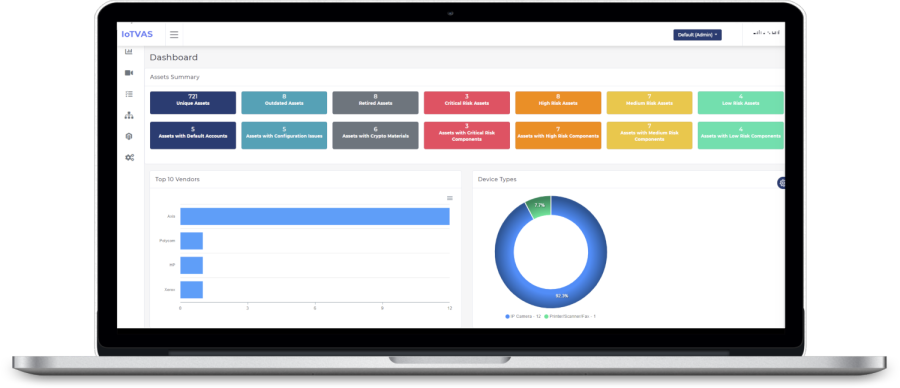
Device discovery
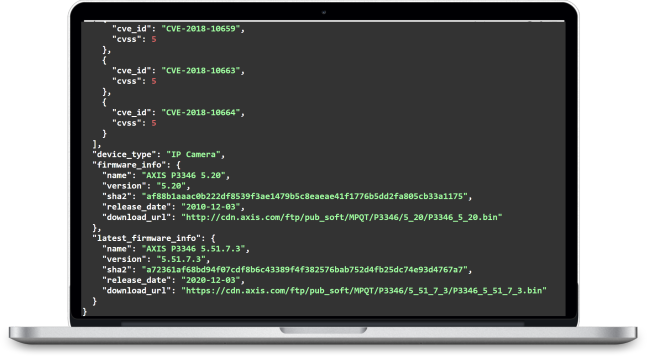
Accurate identification of device manufacturer, model name, device type, firmware version and firmware release date

Firmware risk analysis
Comprehensive vulnerability detection and risk assessment in firmware code level

Configuration risk analysis
Detection of backdoor crypto keys and accounts on devices

Lifecycle risk analysis
Detection of End-of-Life and unpatched devices
Reduce Risk
Proactively identify and fix devices with vulnerable firmware or insecure factory configuration
Reduce Cost
Use your cyber security budget efficiently by integrating IoTVAS API into your existing IT asset management or vulnerability scanning solution
Check Reputation
Check the security posture of the devices manufactured or consumed by your organization
Increase Compliance
Verify and demonstrate compliance of your devices with relevant cyber security standards and guidelines
Boost Productivity
Automate device security assessment on-scale and focus on mitigating risks
Enable New Business
Augment your cyber security solutions with connected device risk analysis via Firmalyzer risk API
Who benefits from Firmalyzer platform
Enterprise
Enterprises begin to notice the immense growth in the number of connected devices such as IP cameras, printers and IP phones in their networks that unlike servers, workstations and laptops cannot be monitored, managed and updated by installing “security agents”. Traditional network scanners often fail to detect even most trivial IoT/connected devices vulnerabilities such as default credentials as they are not equipped with IoT/connected devices specific threat knowledge bases.
Device Manufacturer
connected device manufacturers include software components such as operating systems, drivers and libraries from 3rd party sources in device firmware that could contain security vulnerabilities or insecure cryptographic keys or algorithms. Such vulnerabilities or weaknesses in device firmware could be exploited remotely over the network and put customers at risk.
Risk Management Solution Provider
Third party risk management platforms need to continuously analyze and monitor the security posture of vendors and their products across different risk groups such as vendor's IT infrastructure and product vulnerabilities over time. In the context of connected device vendors, automatic security risk analysis of millions of firmware files across different vendors and device models, is an integral process.
Connected device discovery and vulnerability assessment made automated, proactive and effective
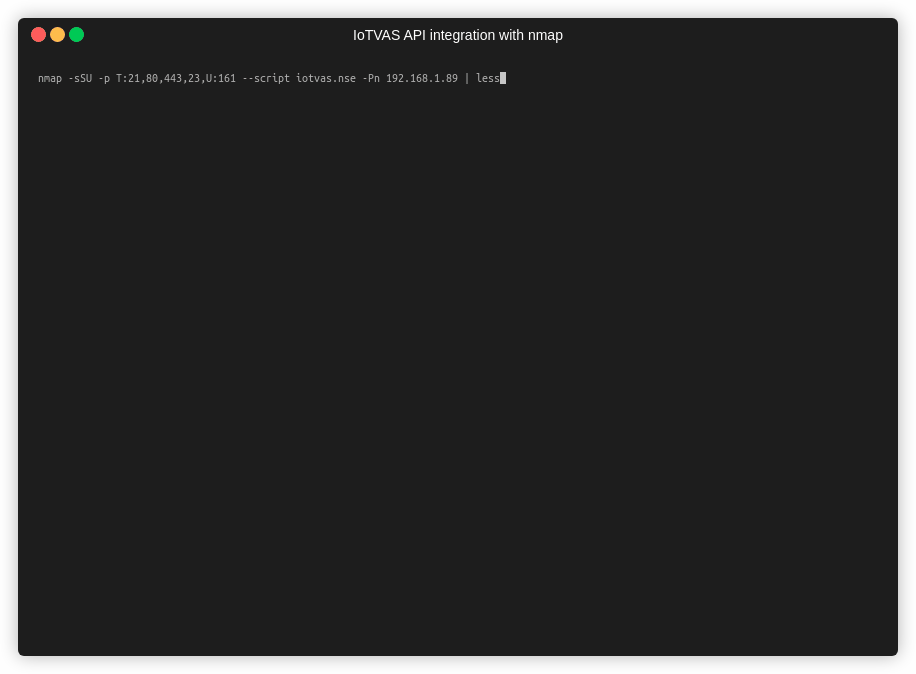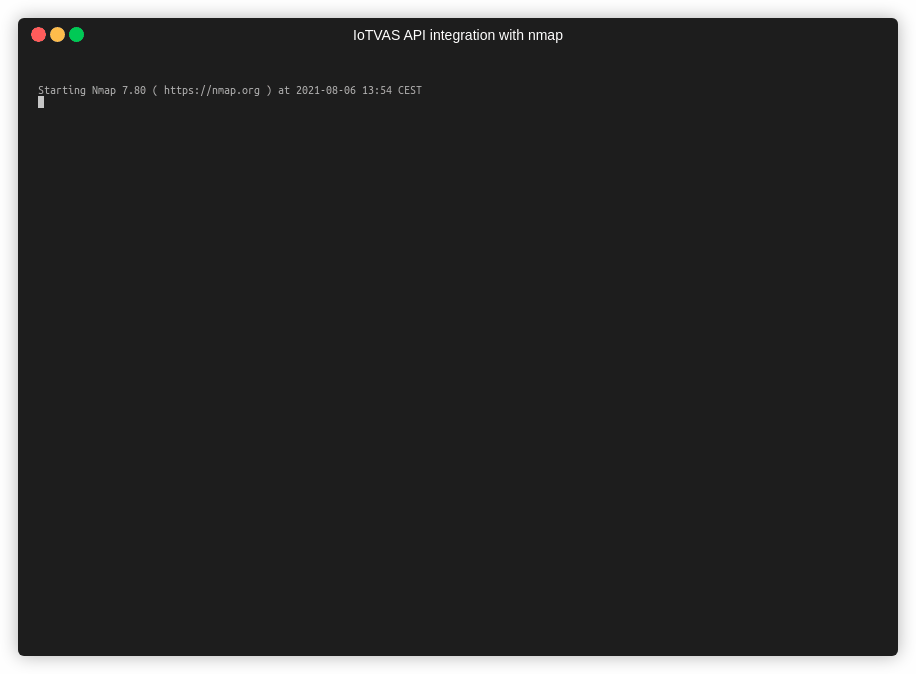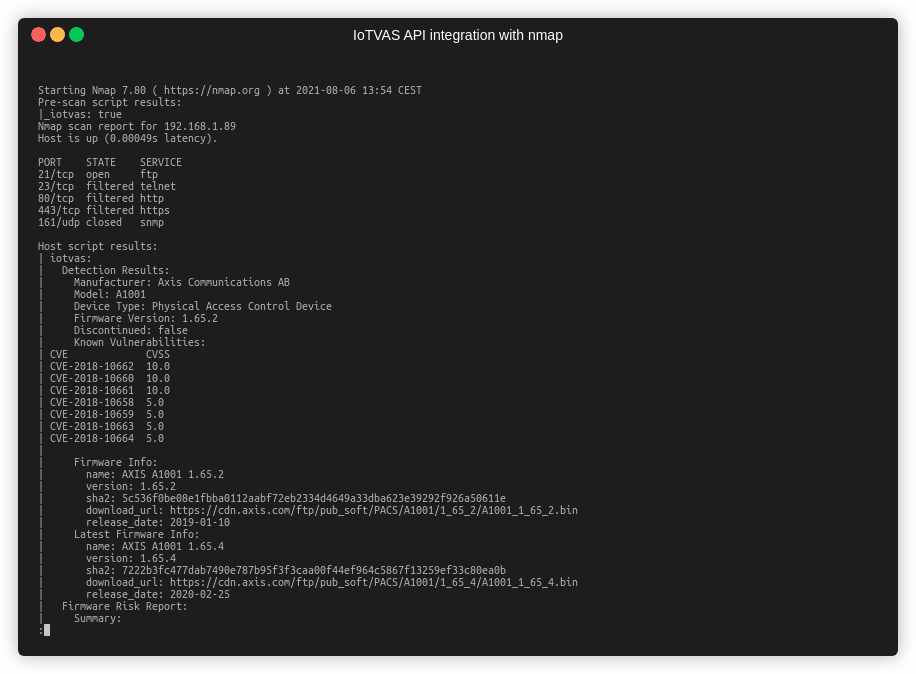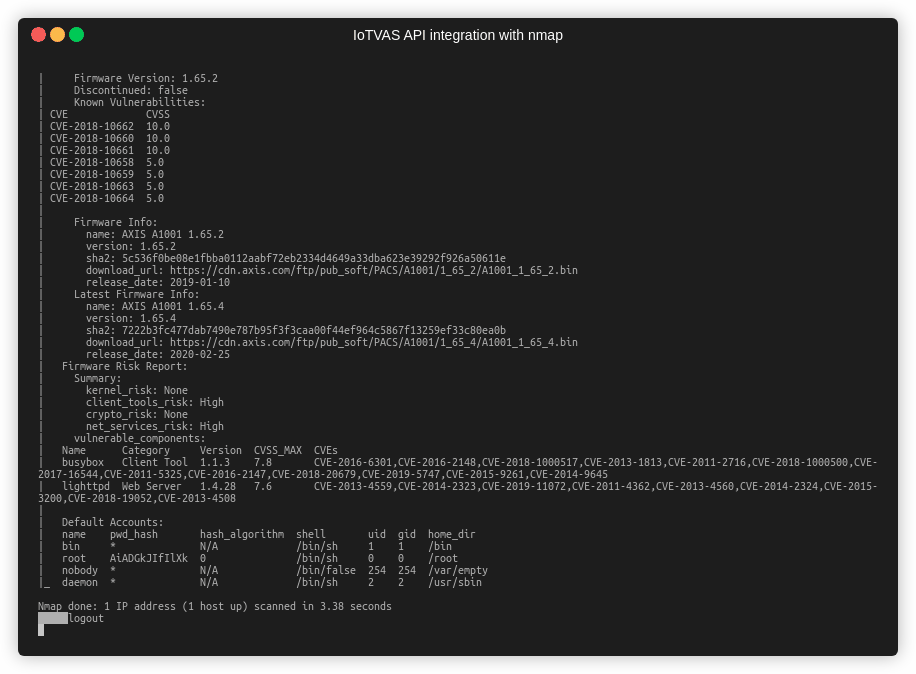
IoTVAS is one of the missing pieces of enterprise security puzzle
Trusted by





From our blog
Integrating IoTVAS API with Qualys Cloud Platform for IoT/connected device discovery and vulnerability assessment
Read moreIntegrating IoTVAS API with Rapid7 InsightVM for IoT/connected device discovery and vulnerability assessment
Read moreIoT/connected device discovery and vulnerability assessment using IoTVAS API
Read more