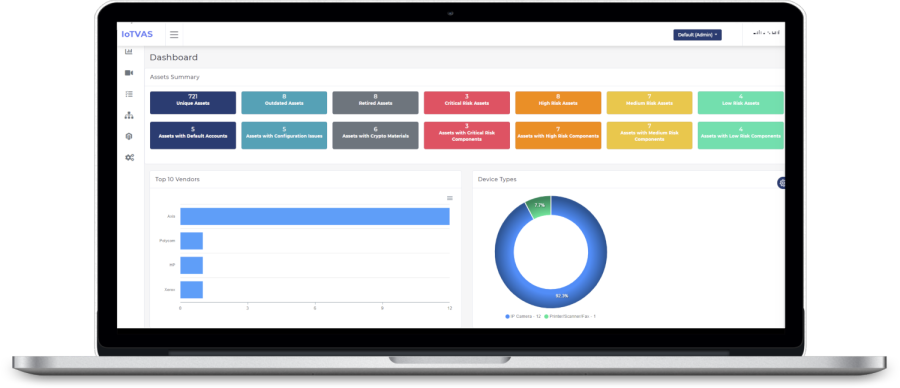
IoTVAS SaaS: IoT/connected device discovery and vulnerability assessment platform
Connected devices can become security blind spots
The number of network-connected devices in enterprise networks is growing which unlike workstations, laptops and servers are not properly identified and monitored by IT security teams within organizations. While many consider these devices to be “simple” in terms of on-board software and networking capabilities, they are not simple at all – most of them run flavours of Linux or a real time operating system included with their firmware that are vulnerable to web application and memory corruption in the same way as servers, desktop operating systems and applications. The only difference is that IT administrators cannot install OS monitoring agents or anti-malware software on OT/IoT devices as they do for their fleet of servers and workstations. This makes these devices a prime landing point, attack pivoting and malware persistence in enterprise networks. Therefore, a compromised IoT/connected device may remain undetected for months while being used as a launchpad for attacking internal hosts or exfiltrating sensitive data.
How does IoTVAS SaaS discover IoT/connected device risks?
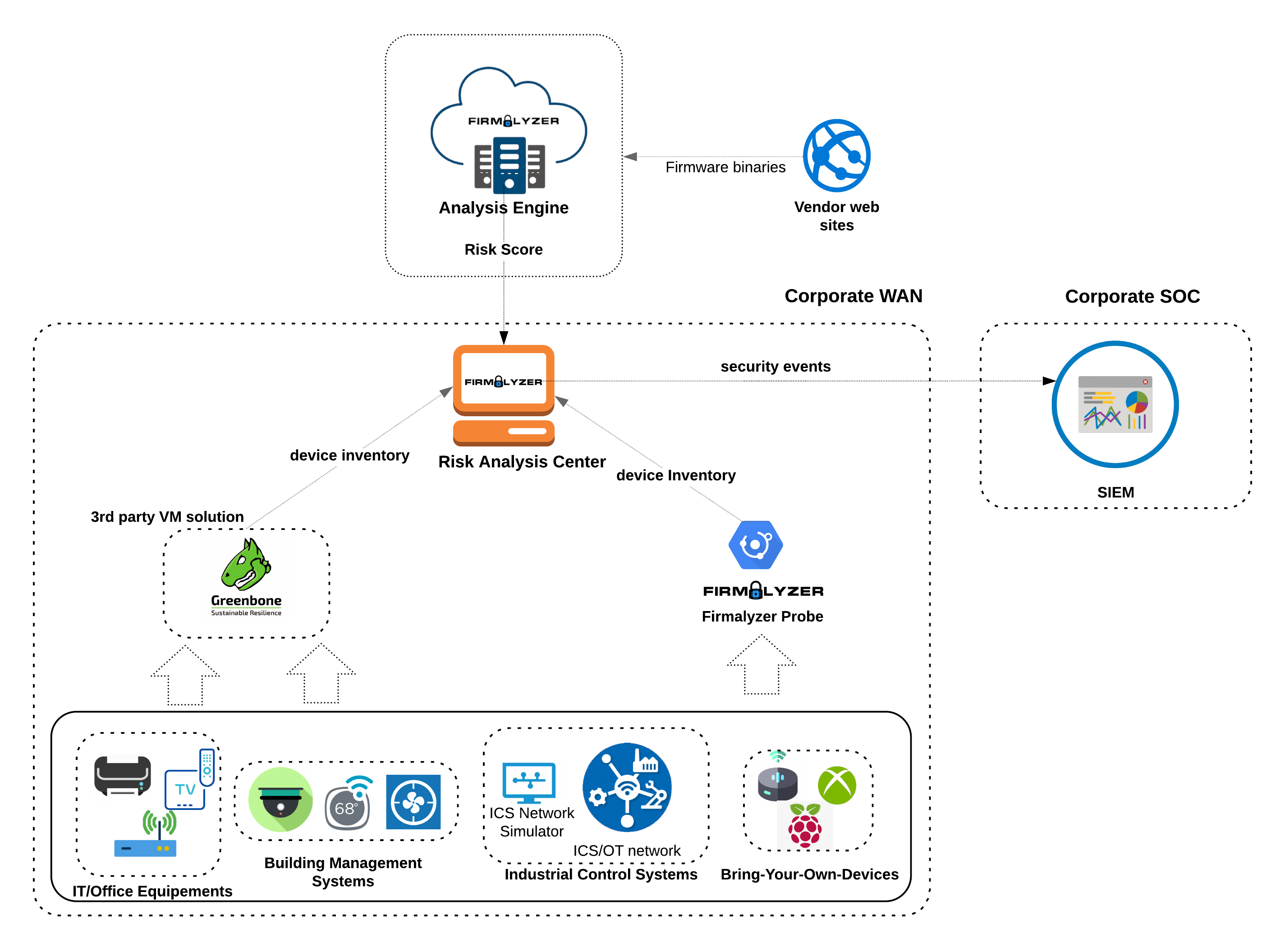
Device Discovery: Firmalyzer probe is a virtual appliance that discovers your connected device assets in the local network or on the internet without network traffic capturing or requiring access to device credentials. It does so by using standard discovery protocols and safely probing network services on devices.
Device inventory retrival: IoTVAS integrates with your existing IT asset discovery or vulnerability management solution to automatically pull the following information for every discovered device:
IoTVAS can be integrated with any asset discovery solution that can discover and expose the above asset information. This includes leading solutions such as Lansweeper and Greenbone Networks.
Vulnerability identification: IoTVAS vulnerability detection engine is specifically built for enterprise IoT/connected device security and is based on our global-scale proprietary firmware vulnerability knowledgebase that is constantly growing and evolving automatically as our analysis engine automatically collects and processes new device firmware binaries on behalf of device manufacturers and consumers. Through this knowledgebase, our vulnerability detection engine gains in-depth visibility into the applications running on a target IoT/connected device, their vulnerabilities and associated risks. IoTVAS also keeps tracking vulnerable devices as they change IP address or move around the network.
Risk Reporting: Vulnerability details and risk scores can automatically be delivered into your SEIM or GRC platform of choice.
Platform Features
Integration with existing IT vulnerability management and network asset discovery solutions
Rapid deployment that does not require installation of network taps or port mirroring
Discovery of known vulnerabilities (CVEs) affecting connected devices
Detection of discontinued/retired IoT/OT/connected devices
Detection of devices that run outdated firmware version
Safe device probing that does not interfere with device operation
Coverage for OWASP IoT top 10 vulnerability classes including:
-
Weak or hardcoded credentials or cryptographic materials
-
Insecure default settings of device operating system
-
Insecure or outdated components
-
Insecure network services