ISO 27002
What is ISO 27002?
The ISO 27002 standard is a collection of information security guidelines that are intended to help an organization implement, maintain, and improve its information security management.
ISO 27002 provides hundreds of potential controls and control mechanisms that are designed to be implemented with guidance provided within ISO 27001.
Many organizations use ISO 27001 and 27002 in conjunction as a framework for showing compliance with regulations. As such the companies utilize various products to control the compliance with the standard.
IoT device security controls by the ISO 27002 standard
The standard includes the following two general control categories:
- 8.1.1 Inventory of assets: Assets associated with information and information processing facilities should be identified and an inventory of these assets should be drawn up and maintained. The control clearly mentions that “the asset inventory should be accurate, up to date, consistent and aligned with other inventories.”.
- 12.6.1 Management of technical vulnerabilities Information about technical vulnerabilities of information systems being used must be obtained in a timely fashion, the organizations exposure to such vulnerabilities evaluated and appropriate measures taken to address the associated risk.
Challenges with the current asset and vulnerability management tools
There are various IoT device assets in enterprise networks that are associated with information and information processing facilities such as surveillance cameras, switches, IP phones, video conferencing systems, etc which according to the standard need to be accurately inventoried and their vulnerabilities must be obtained and managed in a timely fashion. The accurate way of doing this task for IoT devices is by correctly identifying the manufacturer, model and firmware version and then accurately mapping the CVEs to the vulnerable firmware versions installed on the devices. This also facilitates the detection of outdated assets or discontinued assets. However, the current widely used asset and vulnerability management solutions have very limited coverage for IoT devices. There are a very limited number of IoT devices which can be detected at the granularity of the firmware version by those solutions. As such the correct identification of vulnerabilities without detecting the firmware version is not possible. They also do not provide any information regarding the outdated devices or devices that reached their end-of-life.
How can Firmalyzer help?
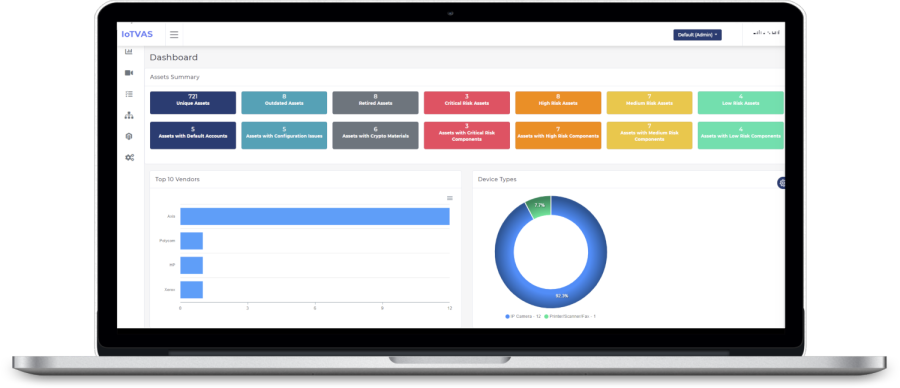
Firmalyzer provides an IoT device discovery and vulnerability assessment solution (IoTVAS) that brings in-depth visibility into IoT devices and their vulnerabilities. The solution can successfully check the controls 8.1.1 and 12.6.1 by:
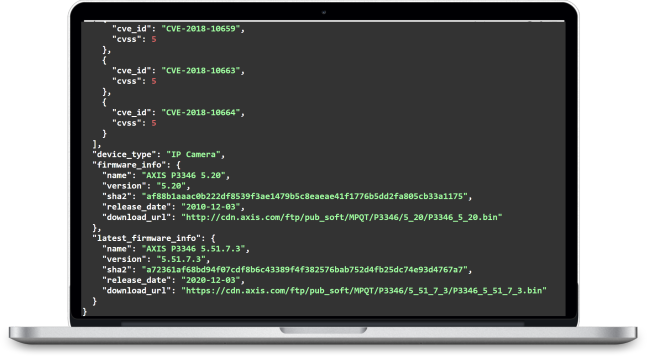
- Detecting devices maker, model and firmware version
- Accurately detecting device and firmware CVEs
- providing in-depth firmware level vulnerabilities and associated risk scores
- detecting discontinued devices
- detecting devices with outdated firmware
IoTVAS vulnerability detection engine is specifically built for enterprise IoT/connected device security and is based on our global-scale proprietary firmware vulnerability knowledgebase that is constantly growing and evolving automatically as our analysis engine automatically collects and processes new device firmware binaries on behalf of device manufacturers and consumers. Through this knowledgebase, our vulnerability detection engine gains in-depth visibility into the applications running on a target IoT/connected device, their vulnerabilities and associated risks. IoTVAS also keeps tracking vulnerable devices as they change IP addresses or move around the network.