IoT/connected device discovery and vulnerability assessment using IoTVAS API
Today’s enterprise networks are complex environments with different types of wired and wireless devices being connected and disconnected. Therefore, an effective device discovery system that enables us to identify device type, maker, model and OS/firmware is crucial for successful security management.
The current device discovery solutions have been mainly focused on identifying and monitoring servers, workstation PCs, laptops and infrastructure devices such as network firewalls, switches and routers. This is due to the fact that the most valuable information assets of organizations are being stored, processed and transferred over those devices, hence making them the prime target of security breaches and intrusions. However, a new trend has been emerging in the past 4 years, where attackers have been targeting purpose-built connected devices such as network printers and video conferencing systems as an entry point and data exfiltration node. IT asset discovery solutions cannot properly identify these IoT devices for the following reasons:
- Proprietary protocols are often used for managing and monitoring such devices that are not known to the asset discovery solution
- Agent based asset discovery is not possible because most of the connected devices are resource constrained systems with proprietary operating systems that do not allow installation of discovery agent software on them
Furthermore, traditional IT vulnerability scanning solutions have limited coverage when it comes to IoT devices:
- Device discovery is often limited to the devices with a history of known vulnerabilities
- The fuzz testing methods used by these solutions often time caused device operating system crash and reliability issues
Firmalyzer IoTVAS API is an IoT device identification and vulnerability assessment API that can be easily integrated with asset discovery, network port scanners and IT vulnerability scanning tools and enable them to perform:
- Accurate identification of IoT device manufacturer, model name, device type, device end of life status, firmware version and firmware release date
- Safe and in-depth vulnerability assessment of identified device including publicly known vulnerabilities (CVE) and unknown vulnerabilities in device firmware code including vulnerable 3rd party components, default credentials, crypto keys, certificates and default configuration issues
In the following section, we demonstrate how to integrate IoTVAS with the NMAP network port scanner, so that it can identify connected devices and their firmware level risk score and detailed vulnerabilities.
IoTVAS NSE Script
IoTVAS identifies devices based on the fingerprints that are derived from device network service banners. The device MAC address can also be used together with this fingerprint to improve detection accuracy but it is not a requirement for IoTVAS unlike the other device discovery solutions. New device fingerprints are continuously added to the IoTVAS fingerprints database, based on the incoming API request and in-house research. At the time of writing this article, this database contains over 50,000 fingerprints for more than 2,300 device manufacturers. IoTVAS uses the following network service response and banners for fingerprint generation:
- SysDescr OID string of the SNMP service
- SysObjectID OID string of the SNMP service
- FTP service banner
- Telnet service banner
- Device host name
- Raw response of the device web server (http and https services)
- UPnP discovery response
- Optional MAC address of device network interface
The API would need at least one of the above values for identifying an IoT device. NMAP can be used as a port scanning front end for extracting those values. We will use NMAP Scripting Engine (NSE) to write such a script and invoke IoTVAS API by using http and json NSE libraries. Our NSE script should have a rule section that declares when NMAP should execute this script and an action section that implements the functionality of the script. The complete source code of IoTVAS NSE script is published here and we will reference source code lines in the rest of this section.
At the beginning of the script, we set prerule and hostrule to check if IoTVAS API key value is provided by the user. We could write the hostrule function to check if the host has active network services of our interest but since we also need to check SNMP service over UDP, we have chosen to do service and port state checks in the action section. We then write host_action to perform the following actions:
- Get response and banners of HTTP, HTTPS, FTP and Telnet services
- Since there was no suitable NSE library to get Telnet service banner, we wrote the negotiate_telnet and parse_telnet_msg functions to start a telnet session and parse server commands up to the banner retrieval
- Get SNMP OID strings using the snmp NSE library
- Determine if there is at least one service banner and if so, call the device detection endpoint of IoTVAS API with the gathered service banners and optional MAC address.
- The device detection endpoint identifies the device type, maker, model and end of life status and known CVEs. It also queries Firmalyzer’s proprietary firmware risk knowledge base for firmware metadata of the device that includes firmware version, SHA2 hash of the firmware image, release date and download URL. The firmware hash can then be passed into the firmware risk assessment endpoint of IoTVAS.
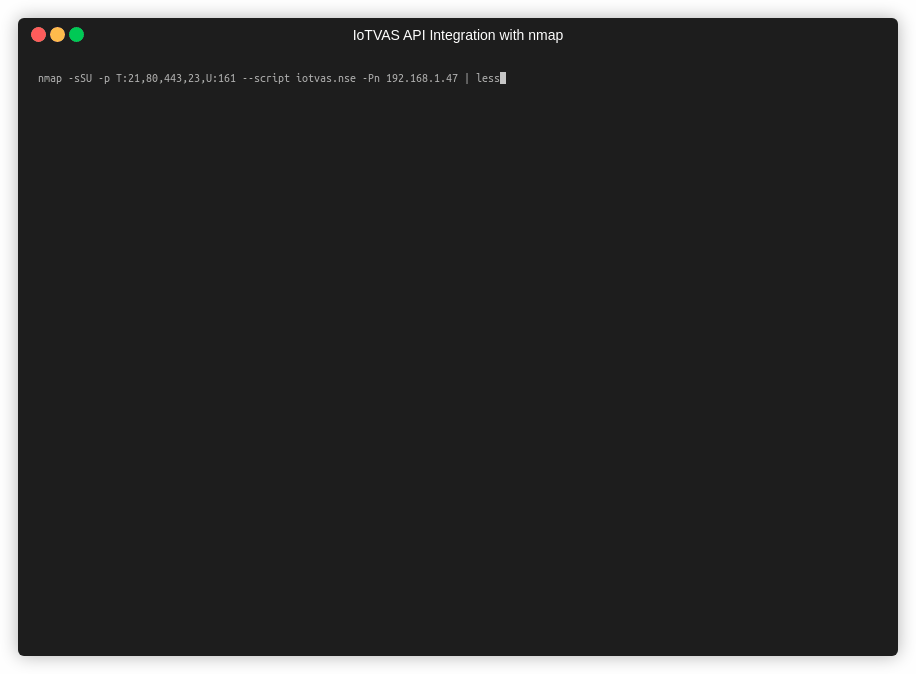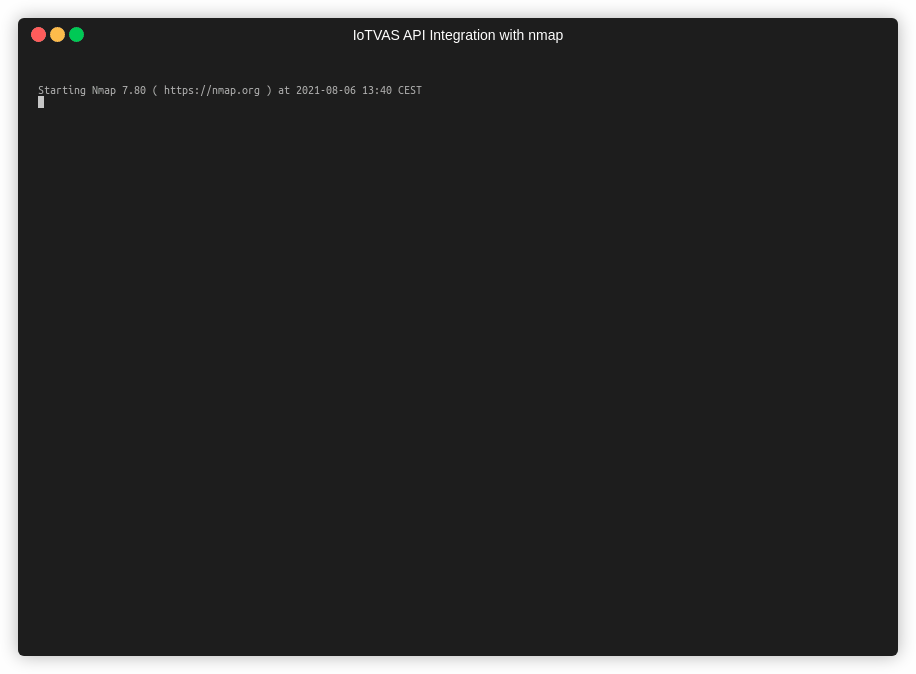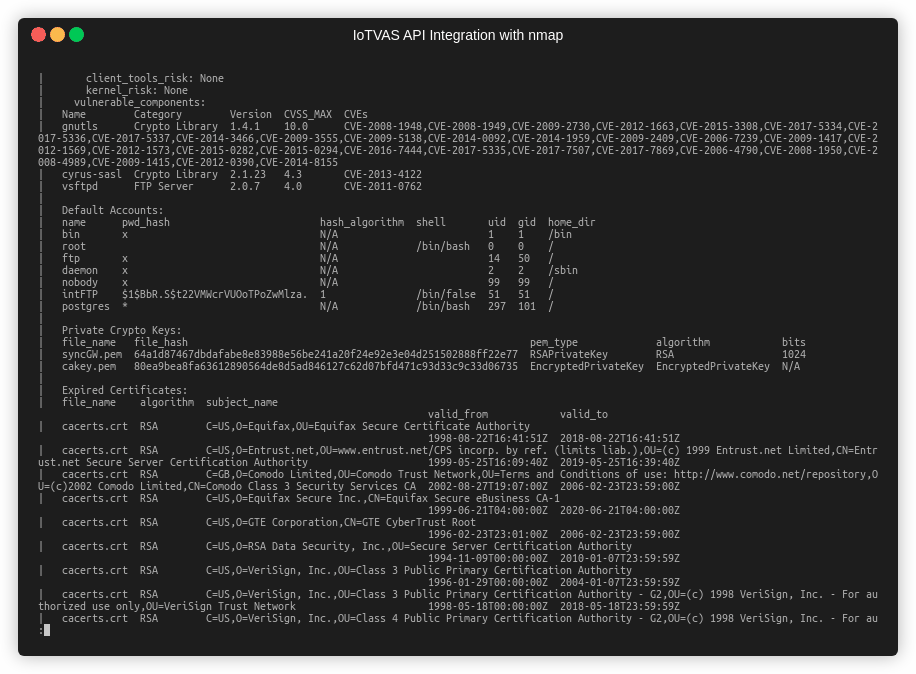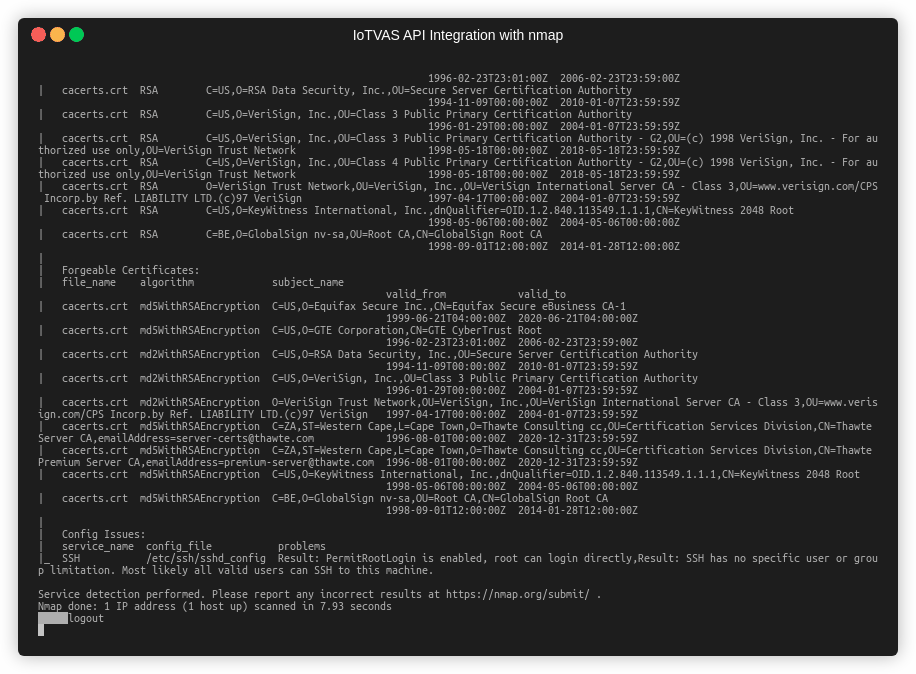
- Finally, we invoke IoTVAS firmware risk analysis endpoints to get the risk score and vulnerability details of the device firmware including vulnerable 3rd party components in the firmware including “network services” such as upnp server, web server, “crypto libraries” such as openssl, “Linux OS kernel” and “client tools” such as busybox. IoTVAS also provides a list of default credentials, crypto keys embedded in the device firmware, active and expired digital certificates, weak crypto keys and certificates and default configuration issues. This in-depth information enables us to proactively detect high risk IoT/connected devices in the network and initiate mitigation efforts before these devices get compromised.
The following figure demonstrates how firmware components analysis capability of IoTVAS would help a user to spot a remotely exploitable vulnerable busybox package (CVE-2016-2148) that is shipped with a building access control management device. Current industry standard vulnerability management solutions fail to offer such in-depth visibility into the vulnerabilities in IoT devices.
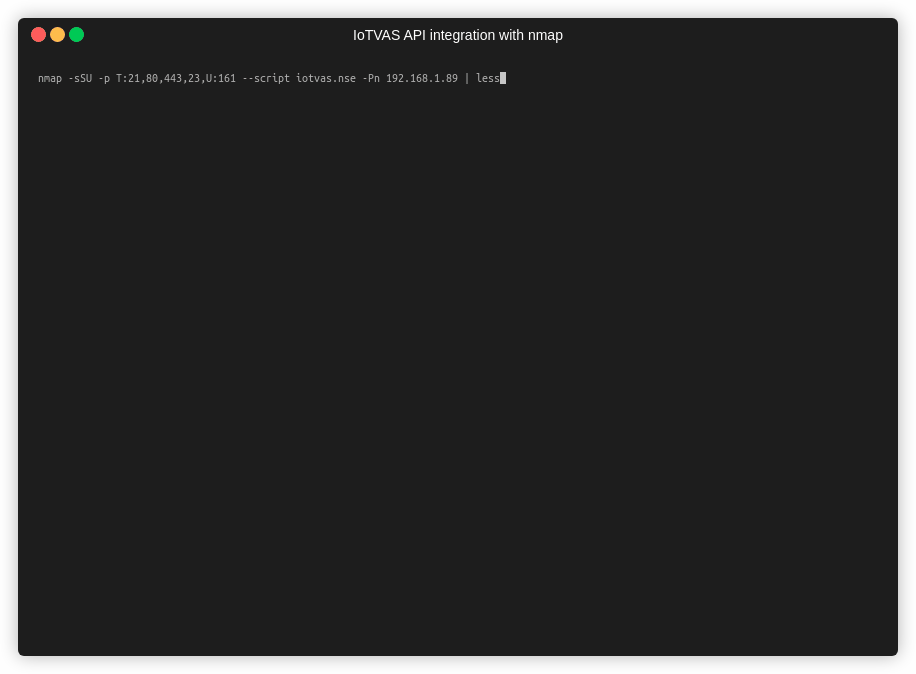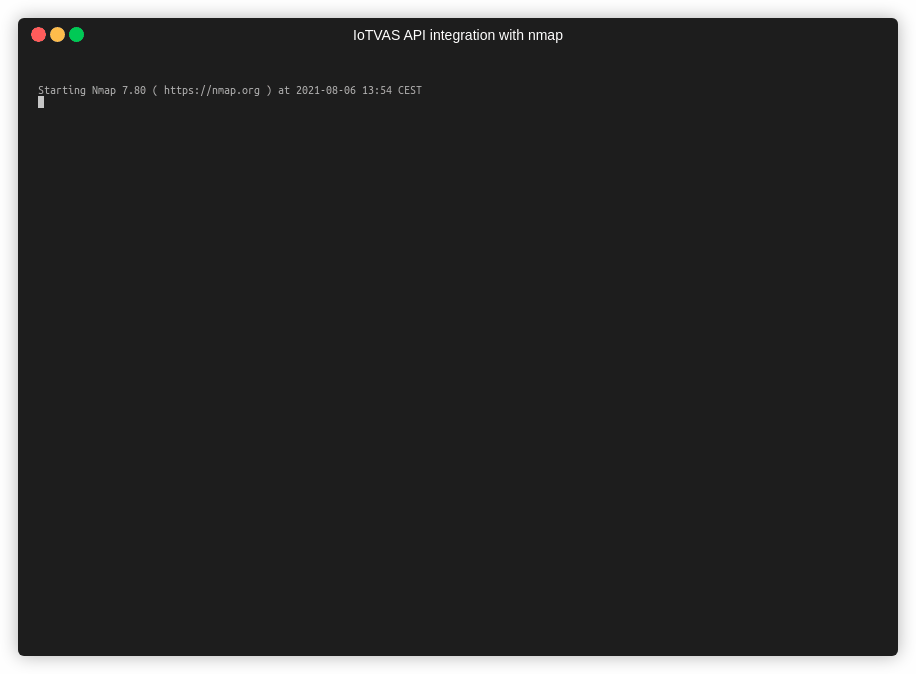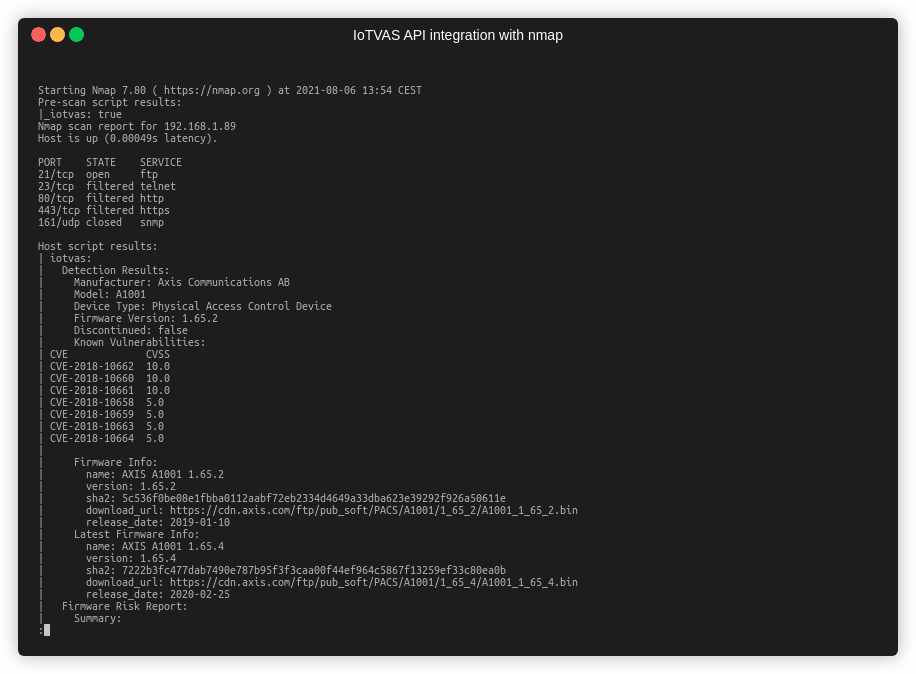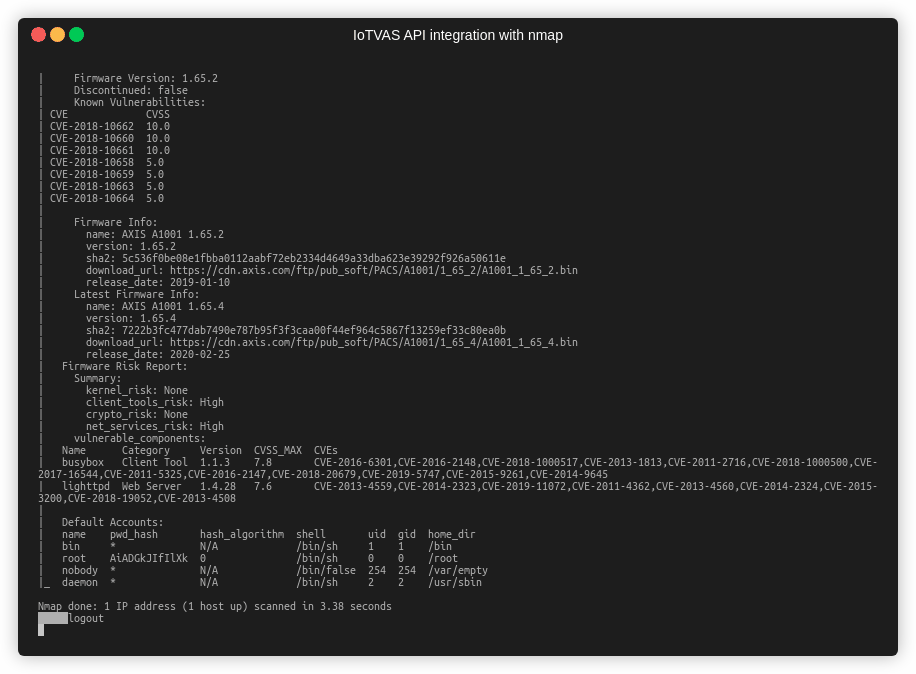
Note that in practice, you do not need to specify the TCP target port range, it can be any range that includes one of the aforementioned services. We would need to expilictly specify UDP port 161, as it is the only UDP based fingerprint we use.
The next example shows how IoTVAS NSE scripts enables NMAP to accurately detect the maker, model name, firmware version of an enterprise printer, along with its known CVEs and firmware risks. The firmware risk analysis reveals “root” and “postgres” default accounts and credential for the “intFTP” account, list of expired certificates and certificates with weak fingerprinting algorithm (MD5) and default configuration of SSH daemon that allows remote root login.
To get started with IoTVAS API, please register for an API key here. The API documentation page includes a swagger UI that allows you to evaluate IoTVAS endpoints right from your browser without writing any code.
The source code of the NSE script and the instruction for running it is available here.
