Firmalyzer discovered a high-severity vulnerability in Mydlink-enabled devices
Affected products:
Mydlink-enabled routers and IP cameras
Vendor homepage:
http://www.dlink.com
Details:
One of Firmalyzer's binary analysis modules is OpenSSL API checker that scans firmware binaries for improper use of OpenSSL APIs such as lack of certificate verification when establishing a TLS connection. Two months ago, Firmalyzer discovered such a vulnerability in a binary named "signalc" included in D-Link DIR-810L "cloud router" firmware.
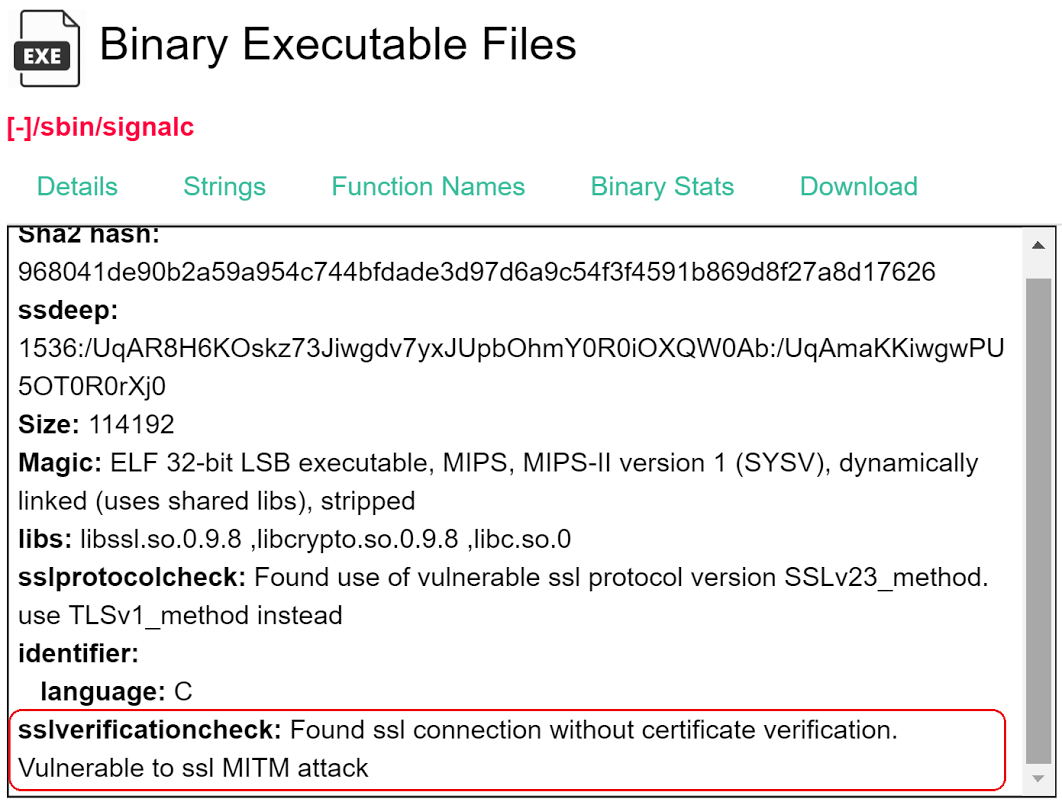
Further investigation indicated that this binary is the "device management agent" for mydlink (https://www.mydlink.com/content/productfamily) line of products that includes IP Cameras, Cloud Storage and Home Routers.The signalc daemon on these devices attempts to establish a TLS connection to mydlink controller server (signal.mydlink.com) on port 443, then registers the device "mydlink ID" and MAC Address and starts listening for commands from controller server (different servers in US and Europe). This commands and control protocol is not HTTP but a proprietary one. The following figure demonstrates the TLS connection establishment using OpenSSL APIs in signalc code:
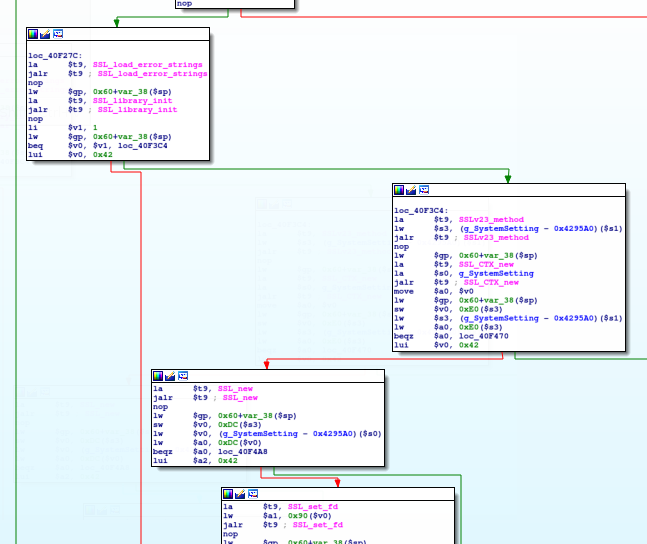
The first vulnerability was the use of SSLv23_method instead of TLSv1_method which causes the agent to accept insecure SSLv2 and SSLv3 handshakes from the server. The second one was lack of SSL_CTX_set_verify API call which should be used to set the callback function for server certificate verification. This could enable an attacker to perform SSL MITM attack in order to capture device credentials sent to mydlink controller server on the internet, inject commands and events into the TLS connection and compromise/hijack all mydlink enabled routers in the reach. The following figures demonstrate such TLS MiTM attack performed on a mydlink enabled DCS-932L IP camera which enables an attacker to capture device admin password sent to the controller server when a) customer registers the device on mydlink portal b) when device admin password is changed:
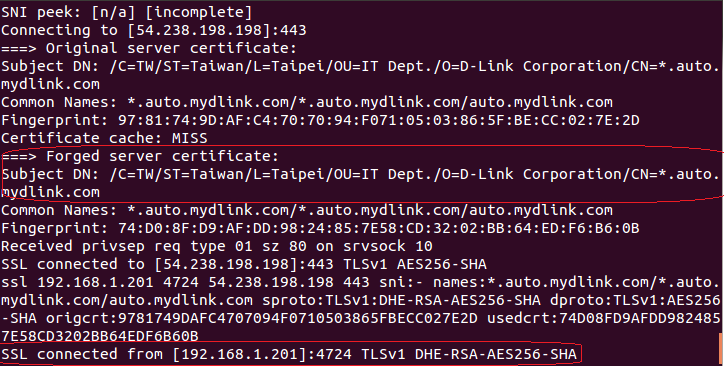

We reported this issue to D-link and worked with them to fix this vulnerability that affects wide range of devices. We advise mydlink device owners to install the latest firmware from D-Link web site and then change their device passwords.
Disclosure timeline:
April 13, 2016 : Vulnerability details sent to D-Link incident response team
April 20, 2016 : D-Link confirmed the vulnerability and requested comments on fix options
April 23, 2016 : Firmalyzer team provided feedback on fix options
June 2 , 2016: D-Link informed us that the fix is ready and will be published on 11 June
June 13, 2016: Firmalyzer advisory is released
